Syngress Penetration Testers Open Source Toolkit Jun 2005 ISBN 1597490210 pdf
Teks penuh
Gambar

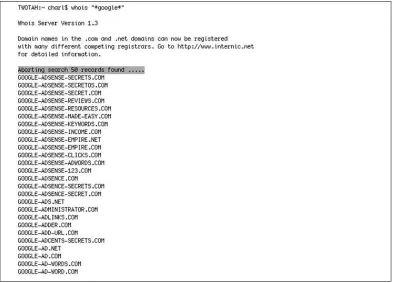
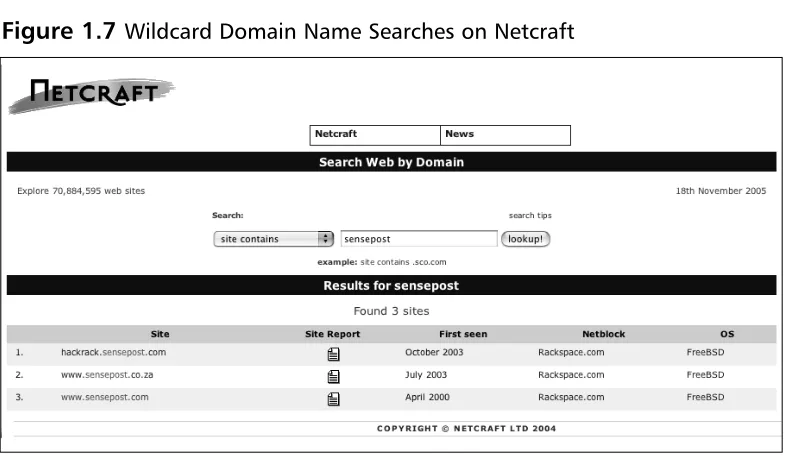
Dokumen terkait
Dinas Perhubungan Kota Palembang melalui Panitia Pengadaan Barang/Jasa Proyek ApBD Kota Palembang Tahun 2011 akan mengadakan Pelelangan Umum dengan Pasca Kalifikasi
Dilihat dari persepsi (PS), mayoritas masyarakat Desa Mendungan bekerja sebagai PNS dan Pegawai Swasta merasa tidak acuh terhadap keberadaan pasar karena tidak memberikan manfaat
bahwa pengendalian atas penyelenggaraan kegiatan pemerintah sebagaimana dimaksud dalam huruf a, dilaksanakan berdasarkan sistem pengendalian intern pemerintah
b) apabila semua harga penaw aran at au harga penaw aran t erkoreksi di at as nilai t ot al HPS, pelelangan dinyat akan gagal. 2) harga sat uan yang nilainya lebih besar dari
Menunjuk Bab III Angka 29 IKP Dokumen Pengadaan, dan sebagai tindak lanjut evaluasi penawaran Pengadaan BELANJA PENGADAAN KONSTRUKSI/PEMBELIAN BANGUNAN (Pekerjaan Pematangan
dipublikasi, dan GLA1 S. Perbedaan residu pengikat pati antara GLL S.fibuligera R64 hasil sekuensing, GLU1 S. fibuligera yang telah dipublikasi, GLA1 S. fibuligera
[r]
Rekapitulasi Belanja Langsung menurut Program dan Kegiatan Satuan Kerja Perangkat Daerah. Rincian Dokumen Pelaksanaan Anggaran Belanja