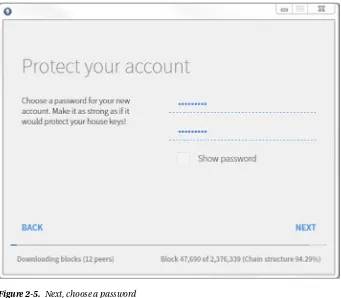
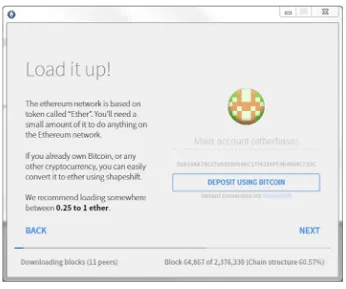
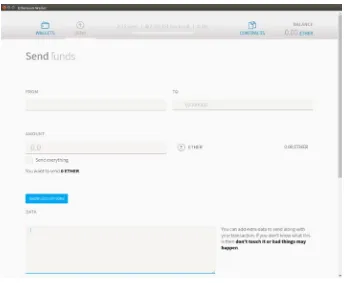
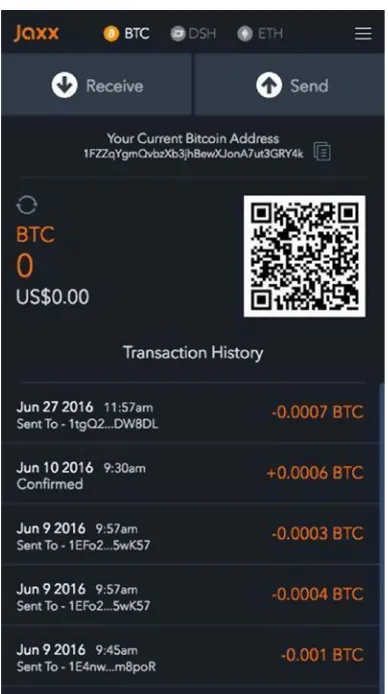
Introducing Ethereum and Solidity by Chris Dannen
Teks penuh
Gambar


Dokumen terkait
Penelitian ini menunjukkan bahwa asupan zat gizi yang meliputi energi, protein, vitamin A, besi, dan seng tidak berpengaruh terhadap perubahan pertumbuhan WHZ bayi sejak lahir
Palu/Vll/2012 tanggal 12 Juli 2412 dan Penetapan Pemsnang Nomor, 15/ULP-Pokja Pengadaan/Dinas PU_Listrik/Kota PaluiVll/2}12tanggal 13 Juli 2412 oleh Pokja ll Pengadaan
KepMdM pMrM peserPM pelelMngMn yMng NerkeNerMPMn MPMs penePMpMn pemenMng ini diNerikMn kesempMPMn unPuk mengMjukMn sMnggMhMn secMrM PerPulis sesuMi kePenPuMn yMng
Margadana Tahap II Kota Tegal Tahun Anggaran 2017 dalam waktu 3 (tiga) hari kalender setelah pengumuman pemenang, terhitung mulai hari Sabtu tanggal 09 September 2017 sampai
Tugas masing-masing kelompok ialah menentukan dan merumuskan/ menyusun substansi-isi materi dari konsep-konsep esensial pada SPB tertentu.. Memantau dan mencermati jalannya
Berdasarkan Dokumen Pengadaan BAB III IKP Pasal 27.2 point j disebutkan bahwa apabila tidak ada peserta yang lulus evaluasi teknis maka pelelangan dinyatakan
Tujuan penelitian ini untuk menganalisis pengaruh dividend per share, retained earning per share dan price earning ratio terhadap kesejahteraan pemegang saham
Kepada peserta yang keberatan terhadap hasil pengumuman ini dapat mengajukan sanggah melalui Aplikasi pada sistem SPSE sesuai jadwal dalam SPSE.. Tanggal 27