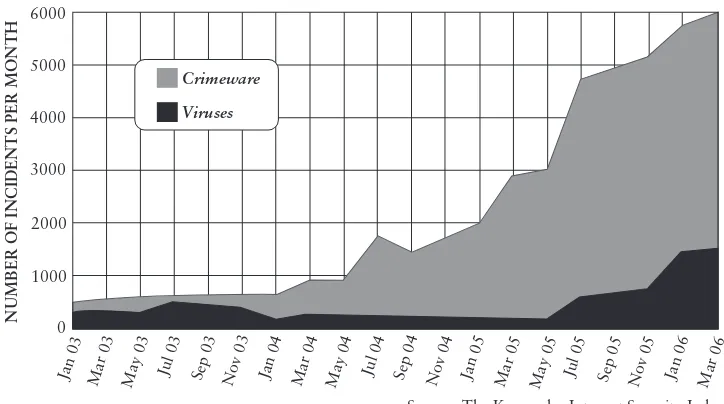
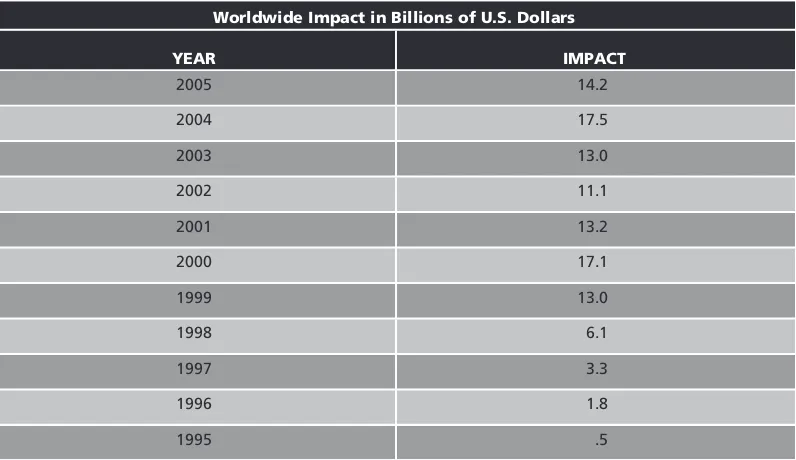
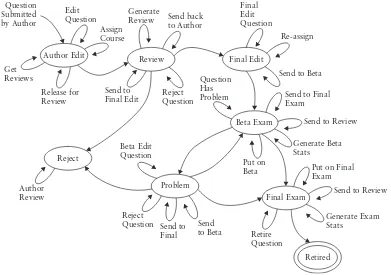
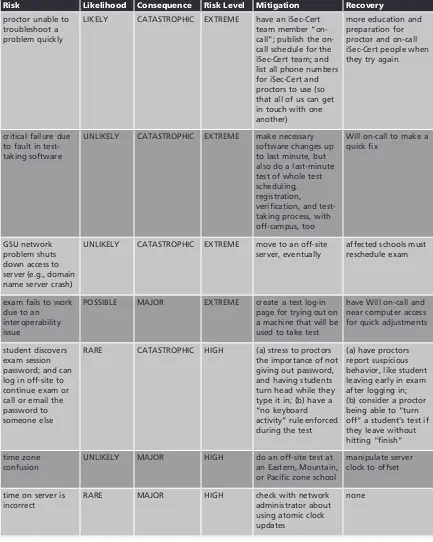
Readings & Cases in Information Security Law and Ethics pdf pdf
Teks penuh
Gambar

Dokumen terkait
It is important to consider the category "security" also in a separate context considering the important component of the security in the structure of the
The framework (ISF) has led us to develop ISM as a user interface between the stakeholder and ISF’s approach to measur- ing information security awareness (ISA) and compliance level
Information Access Policy Objective Control access to information [A.11.1.] Policy Statement ~ Access to information shall be controlled on the basis of business and security
The purpose of this audit IS are : Ensure the asset security of information system in • the company Give the faith of asset information system include • hardware, software,
Amco Enterprise Limited acknowledges that information requires protection against threats to its privacy and security, integrity, and accessibility, and that the safeguarding measures,
Topics include the role of libraries and library organizations with literacy and information access; global challenges such as language, access to resources, the digital divide, and
Information System Security and Risk Management: Issues and Impact on Organizations Shikha Gupta1, Anil K Saini2* 1 School of Computer Applications, Ansal University, Gurgaon,
So it can be said the Digital Security Act 2018 is established to ensure the protection of information of any individual, information of state or information of any public organization