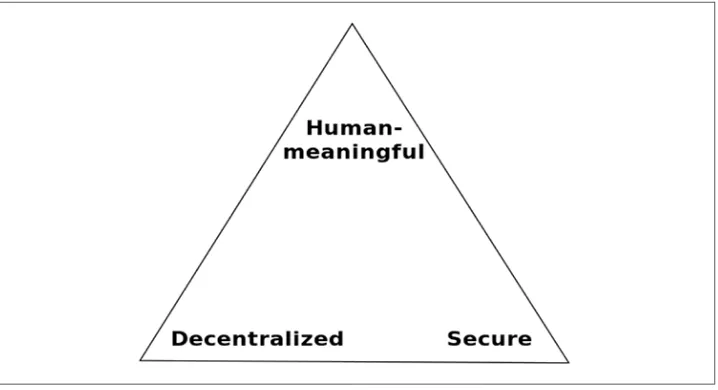
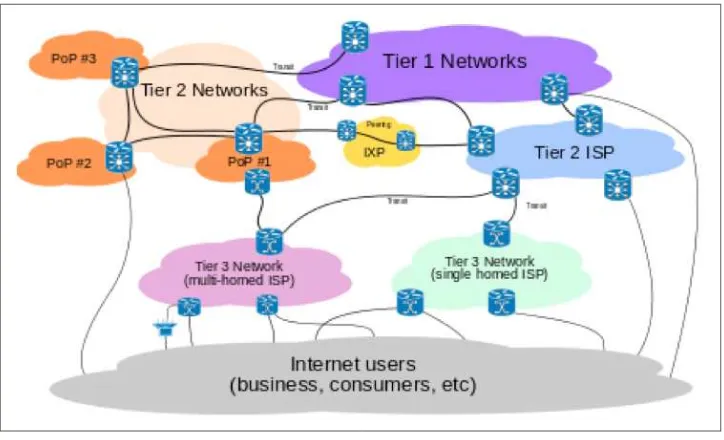
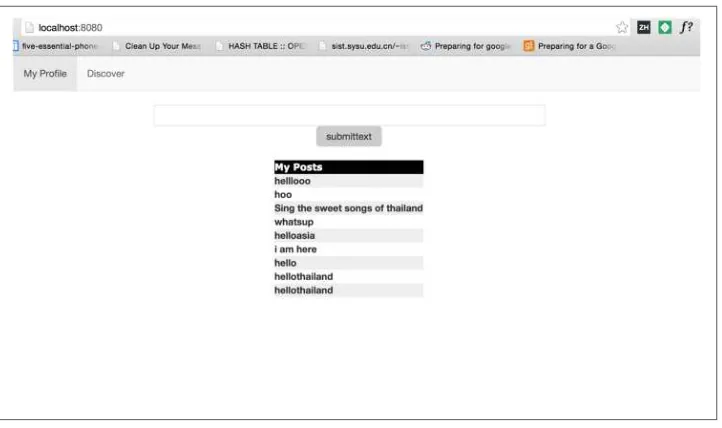
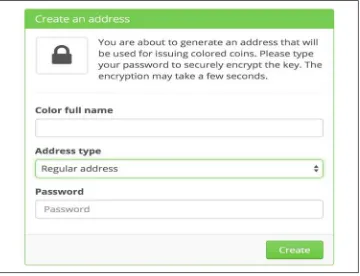
Decentralized Applications by Siraj Raval
Teks penuh
Gambar
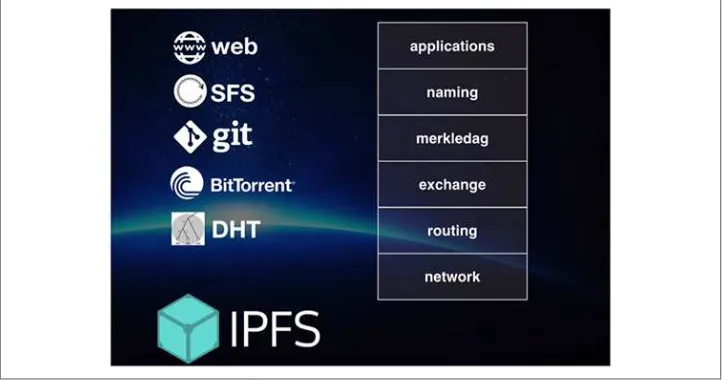
Garis besar
Dokumen terkait
Sehubungan dengan tahap evaluasi dan pembuktian kualifikasi dalam proses pengadaan Pekerjaan Saluran Drainase Jalan Beringin, dengan ini kami mengundang Saudara untuk
Implikasi dari hasil penelitian ini ialah bahwa dalam membuat perangkap feromon dengan perangkat ember seperti pada Gambar 1, bagian papan yang berfungsi untuk
[r]
Aspek yang masih perlu ditingkatkan oleh guru dalam proses pembelajaran pada siklus I adalah mengorganisasikan siswa dalam kelompok belajar, membimbing kelompok belajar
Demikian disampaikan, untuk diketahui. Ahmad
Berupa Pembuatan Lantai Sintetik Outdor dan Pendukungnya pada Kementerian Pemuda dan Olahraga Tahun Anggaran. 2014., dengan total HPS/OE sebesar Rp.2.786.564.000,-(Dua milayar
[r]
X.k.6 tentang kewajiban penyampaian laporan tahunan bagi emiten atau perusahaan publik, dengan ini kami, Dewan komisaris dan Direksi pt semen gresik (persero) tbk,