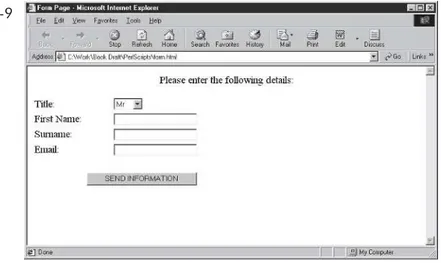
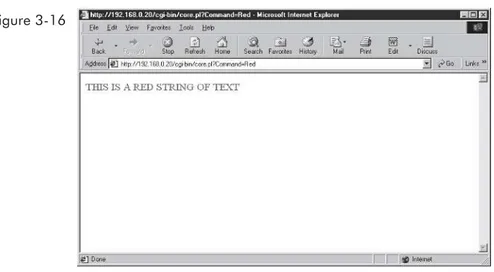
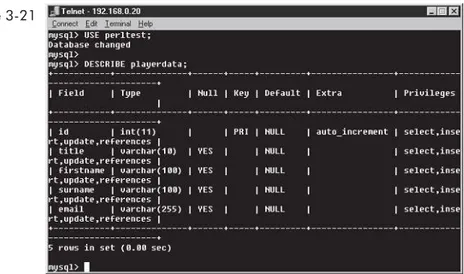
Developer's Guide to Multiplayer Games pdf
Teks penuh
Gambar




Garis besar
Dokumen terkait
Jika dalam waktu yang telah ditentukan Saudara tidak hadir, dianggap telah menerima segala keputusan Pokja Jasa Konstruksi 1 (satu) - ULP Tanjung Jabung Timur.. KELOMPOK KERJA
Kedua , temuan ini mendukung hasil temuan dari Wasino 95 yang menegaskan bahwa kapitalisme Jawa khususnya pada pengelolaan lahan tebu dan pabrik gula
Departemen Kesehatan RI Konseptual Framework Provincial Health Account (PHA), District Health Account (DHA) bersumber Pemerintah, Biro Keuangan Departemen Kesehatan RI,
Nilai modulus penampang teoritis diperoleh dengan asumsi bahwa penampang yang memiliki sambungan finger joint tidak memberikan kontribusi pada balok laminasi sedangkan
Dengan perhatian yang penuh dan bimbingan yang intensif dari orang tuanya sebagaimana telah dijelaskan di atas, berdasarkan survei dan observasi yang dilakukan
Brand Image Kawasan Maribaya Sebagai Objek Wisata Berwawasan Lingkungan (Ekowisata) Universitas Pendidikan Indonesia | repository.upi.edu..
Yang dimaksud dengan “per bulan” pada ayat ini adalah 30 (tiga puluh) hari kalender setelah surat Sanksi Administratif Berupa. Denda ditetapkan atau 30 (tiga puluh) hari
apabila Saudara tidak hadir sesuai jadwal tersebut diatas dengan alasan yang tidak dapat diterima, maka perusahaan Saudara beserta pengurusnya dimasukkan ke dalam Daftar Hitam