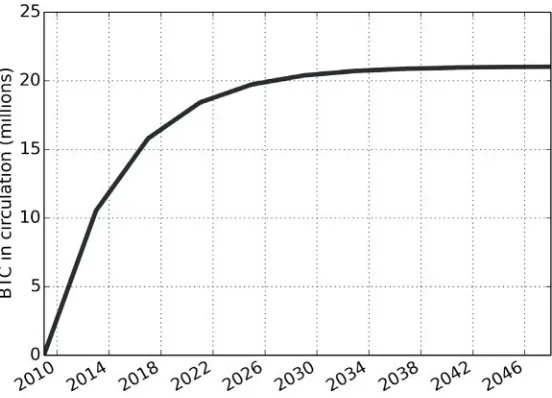
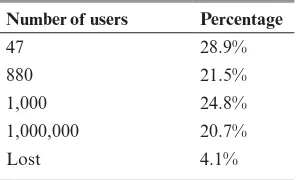
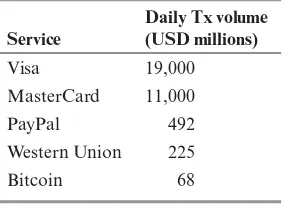
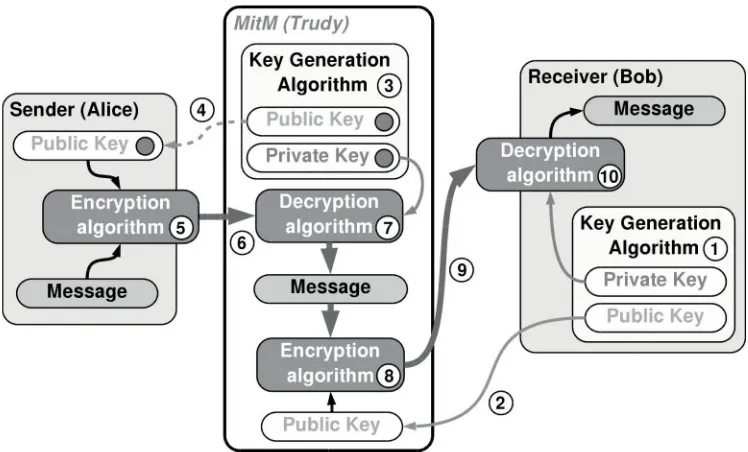
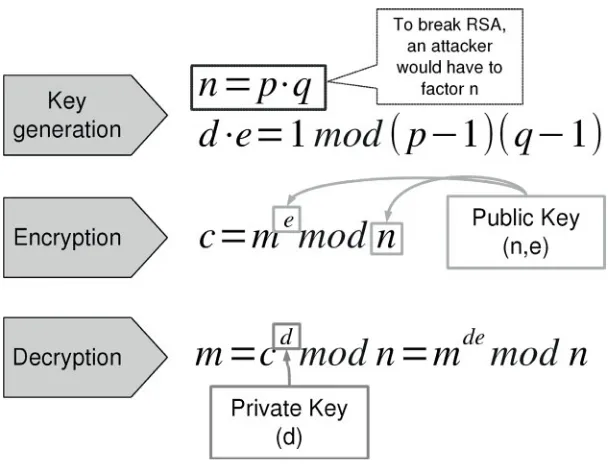
BitCoin and Cryptocurrencies Wiley .Understanding Bitcoin Cryptography. Engineering.and.Economics.Nov.2014
Teks penuh
Gambar

Dokumen terkait
Along with the conclusions, propose the following suggestions: (1) the school management should monitor the performance of teachers through classroom
Telah dikembangkan model bahan ajar, yang karakteristiknya, didasari pada karak- teristik pelajaran fisika sesuai dengan tuntutan kurikulum 2013 dari sisi konten,
Perilaku kepala sekolah yang mampu memprakarsai pemikiran baru dalam proses interaksi dilingkungan sekolah dengan melakukan tujuan, prosedur, input, proses dan
Data yang digunakan dalam penelitian ini adalah data sekunder dari perusahaan di Indonesia yang melakukan proses akuisisi selama periode 2009- 2012 meliputi
Supervisi Pengembangan supervisi akademik melalui kunungan kelas Kinerja Guru rendah prestasi siswa turun Evaluasi Supervisi Perencanaan Supervisi Pelaksanaan
Dari penelitian ini dapat disimpulkan bahwa penelitian ini berhasil memanfaatkan limbah ampas tebu dan kulit durian menjadi kandidat bahan bakar padat berupa briket hibrida
[r]
1st Annual Applied Science and Engineering Conference I OP Publishing IOP Conf.. Figure 2 is the flow chart of instrument program to measure the speed of kick using