Designing Usable and Secure Software with IRIS and CAIRIS pdf pdf
Bebas
276
0
0
Teks penuh
Gambar
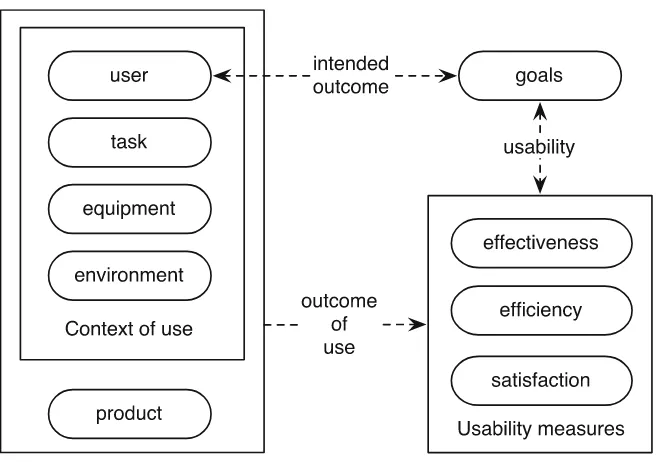
![Fig. 2.2 Human-centered design activities [52]](https://thumb-ap.123doks.com/thumbv2/123dok/3935057.1878477/43.439.57.386.50.351/fig-human-centered-design-activities.webp)
![Fig. 2.3 Example of a security requirement (modelled as an ellipse) constraining a context, mod-elled as a problem frame diagram [98]](https://thumb-ap.123doks.com/thumbv2/123dok/3935057.1878477/50.439.57.383.54.257/example-security-requirement-modelled-ellipse-constraining-context-problem.webp)
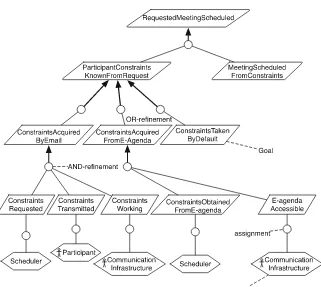
+7
Dokumen terkait