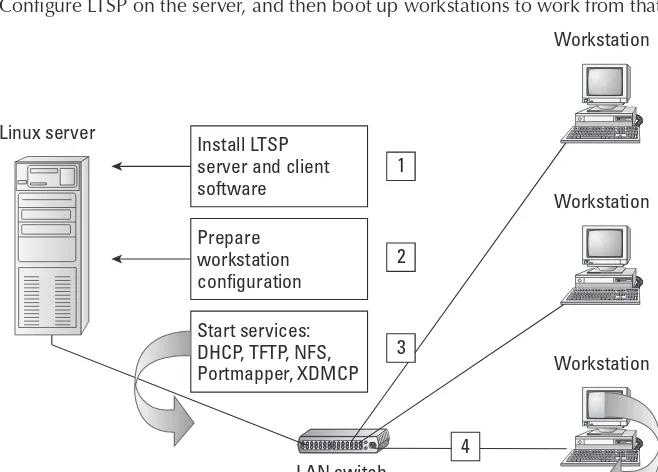
Wiley Linux Bible 2009 Edition Boot Up Ubuntu Fedora KNOPPIX Debian OpenSUSE And More Jan 2009 ISBN 0470373679 pdf
Teks penuh
Gambar


Dokumen terkait
Berdasarkan uraian permasalahan, maka tujuan penelitian ini adalah untuk menganalisis Pengaruh daya tarik wisata dan kualitas pelayanan terhadap minat berkunjung ulang
Pejabat Pengadaan Barang/Jasa Kegiatan APBD pada Bagian Administrasi Pembangunan dan Perekonomian Sekretariat Daerah Kabupaten Musi Banyuasin Tahun Anggaran 2012, berdasarkan
Demikian Pengumuman Pelelangan ini dibuat dan ditandatangani pada hari, tanggal dan bulan sebagaimana tersebut di atas untuk dapatnya dimaklumi..
Hasil yang didapat sesuai dengan kepustakaan bahwa adanya infeksi lain yaitu demam tifoid, varisela, morbili, dan pertusis dapat menyebabkan imunosupresi
Sehubungan dengan telah memasuki tahap pembuktian kualifikasi terhadap dokumen kualifikasi yang saudara sampaikan, maka bersama ini kami mengundang saudara untuk dapat hadir pada
Maka orang-orang yang suka meninggalkan shalat atau mengerjakan shalat di luar waktunya, diancam dengan siksaan di neraka jahannam, sedang orang yang bertaubat dan beramal
Jika semua hal yang dilakukan seorang muslim selama hidupnya di dunia adalah untuk beribadah, maka dalam hal persepsi, yang merupakan anteseden dari niyat beli atau
Bahasan berikut akan mencakup berbagai ha1 yang terkait dengan keselamatan dan kesehatan kerja dan pada bagian akhir akan dibicarakan secara ringkas bentuk-bentuk