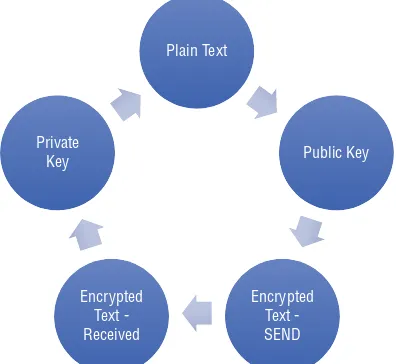
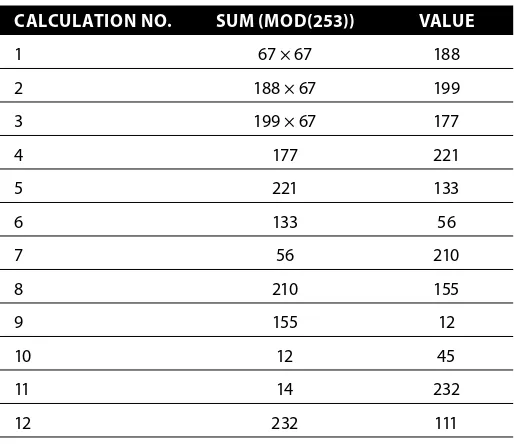
Investigating Cryptocurrencies by Nick Furneaux
Teks penuh
Gambar


Garis besar
Dokumen terkait
Kegiatan rutin adalah melakukan pencatatan data yang ada dalam lingkup peternakan tersebut dengan fokus pada bidang manajemen perkandangan yang dikumpulkan
Hasil penelitian ini menunjukkan bahwa dengan menggunakan metode demonstrasi dapat meningkatkan pemahaman siswa terhadap sifat-sifat benda cair pada pembelajaran sains di
3) Pembuktian kualifikasi untuk menilai pengalaman yang sejenis dan besaran nilai pekerjaan yang sesuai dengan nilai pekerjaan yang akan dikompetisikan dilakukan dengan
Nomor : 30/09/POKJA-BLPBJ.MKS/VIII/2017 tanggal 14 Agustus 2017, kami Pokja 3 Bagian Layanan Pengadaan Barang/Jasa (BPLPBJ) Kota Makassar, dengan ini
Nyeri post operasi merupakan adanya trauma fisiologis pada individu yang terjadi akibat adanya sifat prosedur pembedahan, letak insisi dan kedalaman nyeri sebagai suatu
Perawat atau Petugas Kesehatan di Puskesmas Jetak Kabupaten Tuban Diharapkan dari hasil penelitian ini dapat digunakan sebagai salah satu pedoman bagi perawat dalam
Istilah "belajar" merupalcan sesuatu yang telah biasa didengar dalam pembicaraan sehari-hari. Istilah belajar selalu dikaitkan dengan suatu kegiatan membaca atau
Hal-hal yang harus diperhatikan dalam penapisan kedelai toleran salinitas adalah: (1) Pengawasan/kontrol kondisi media dan lingkungan dilakukan dengan pengukuran DHL tanah/ media