OpenSSL Cookbook Ebook free download pdf pdf
Teks penuh
Gambar
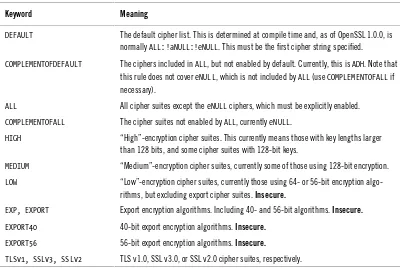
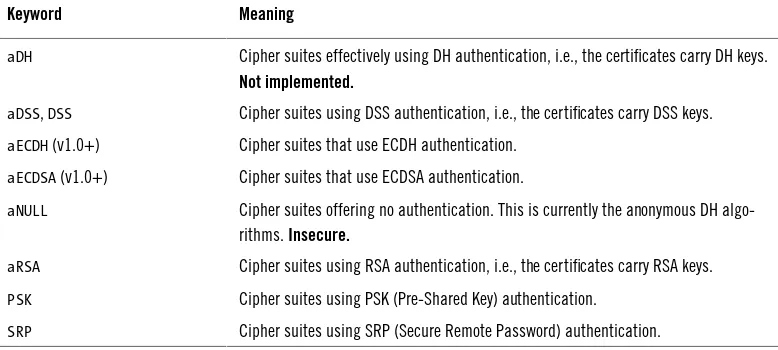
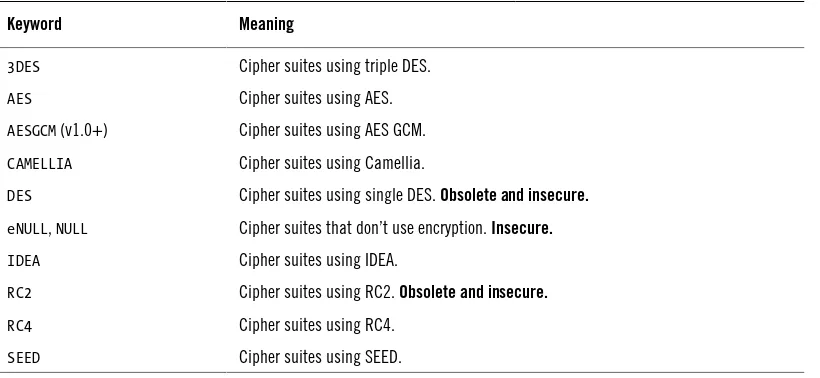
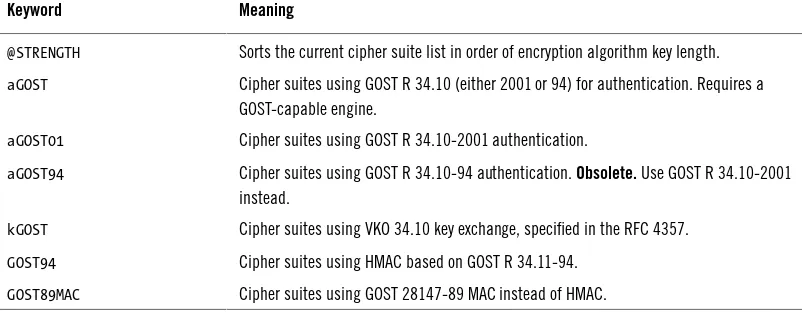
Garis besar
Dokumen terkait
Choose the category and project first and then select one or more scripts that you want to create the schedule with. Use Shift + click to select scripts in a sequence or Ctrl
Our Virtual PostScript Printer driver is simply an INF file instructing Windows to combine this core with the (freely distributable) PPD from Adobe that describes the Acrobat
For simplicity, there was a global Single , but it doesn’t need to be global; you can always create the constructor in a namespace like APP.Single
The ways in which people experience the surface of entities (physical, but potentially digital as well) is important in architecture and product design, and can be used
Just like with a replication controller, the use of a label selector lets us keep fluid which pods will service which request.. Since pods will be created and evicted with
A myriad of options is available when doing port forwarding like this; for example, because many of the systems in my network do not normally run telnet , I could forward
Install Groovy as described in one of the installation recipes (see the Installing Groovy on Windows recipe and Installing Groovy on Linux and OS X recipe) and you'll get the
To open a Spring application that uses Gradle, from the top level ‘File’ menu select the ‘Import...’ option, click on the ‘Gradle’ icon and select the ‘Gradle