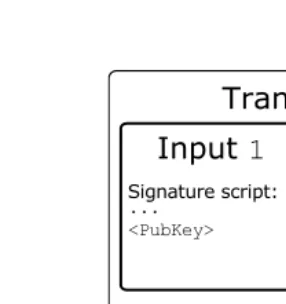
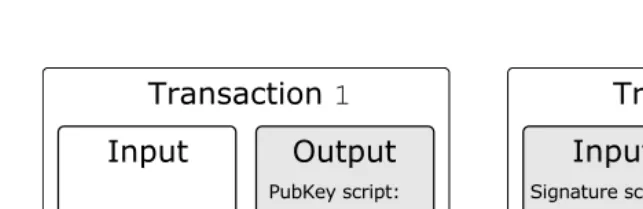
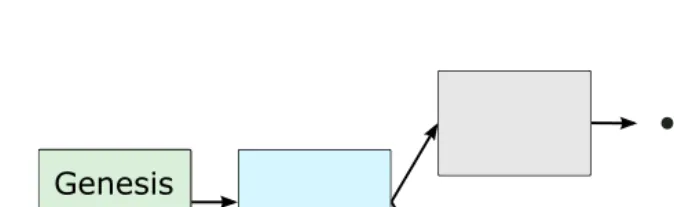
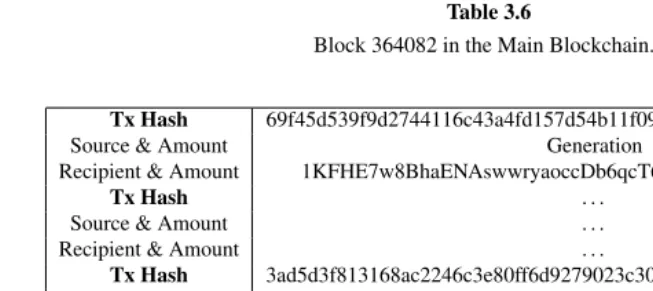
Bitcoin and Blockchain Security pdf pdf
Teks penuh
Gambar
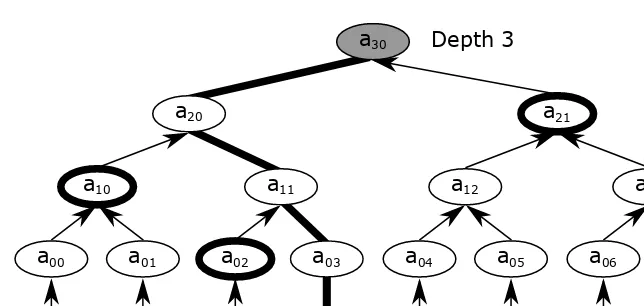
Garis besar
Dokumen terkait
Lansekap Jalan Bebas Hambatan (dalam uraian ini selanjutnya disebut sebagai jalan) adalah wajah dari karakter lahan atau tapak yang terbentuk dari elemen alamiah
program ADD ini di Desa Liang Butan Krayan adalah : (1) Letak geografis Desa Liang Butan Krayan yang jauh berada di pedalaman dan hanya bisa dicapai melalui pesawat udara,
Universitas Negeri
Adanya benang merah antara sistem pemerintahan dalam Penjelasan dan sistem pemerintahan dalam Batang Tubuh Undang- undang Dasar 1945 ini menunjukkan bahwa Soepomo, dengan
Laporan Tugas Akhir ini dibuat sebagai salah satu syarat kelulusan yang sesuai dengan tugas yang diberikan oleh Diploma III Teknik Informatika, Fakultas Teknologi
Tabel 7 menunjukan bahwa interaksi antara suhu pengeringan dengan jenis jagung menunjukkan bahwa suhu pengeringan 60 o C dan 70 o C pada jagung manis dan jagung
Profile Matching menghasilkan nilai ranking berdasarkan selisih nilai pembobotan karyawan dengan kriteria, sedangkan AHP berdasarkan perbandingan nilai hasil iterasi matriks
Circle game can encourage the students to study English well because teaching vocabulary by using circle game the students are given stimulus, such as questions that encourage them