Introduction to E commerce commer ecommerce e-commerce
Teks penuh
Gambar

Dokumen terkait
Then student has investigated possible opportunities of implementing an E-Commerce system to the chosen organization evaluating a current E-Commerce solution used by a
possibilities of hiding transactions are vast and the possibilities of identifying the parties to a transaction are in many cases virtually non-existent and this creates tax
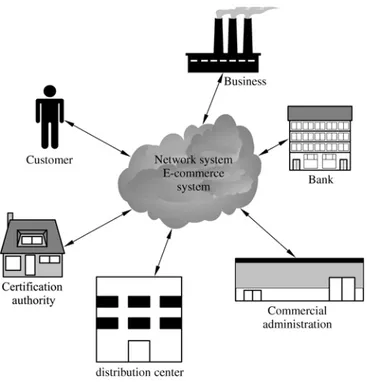
Electronic commerce (EC or e-commerce) describes the process of buying selling, transferring, or exchanging products, services, or information via computer network, including
Abstract: This research paper describes the invention and accessibility of internet connectivity and powerful online tools has resulted a new commerce area that is e-commerce
The use of the internet especially web applications called electronic commerce e-commerce based on Yii framework can help customers to make transactions and find out information about
The use of the internet especially web applications called e- commerce commerce e-commerce based on Yii framework can help customers to make transactions and find out information about
From the description above, this research paper is based from two assumptions, namely: 1 The low level of consumer’s trust to purchase or make transactions through e-commerce websites
Alliance for Global Business, a leading trade association defines e-commerce as all value transactions involving the transfer of information, products, services or payments via