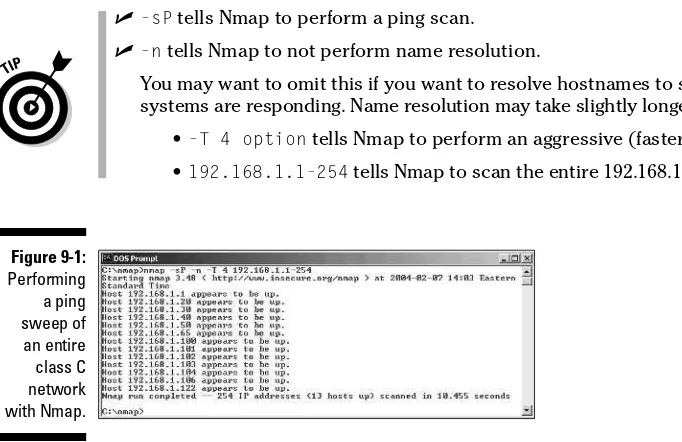
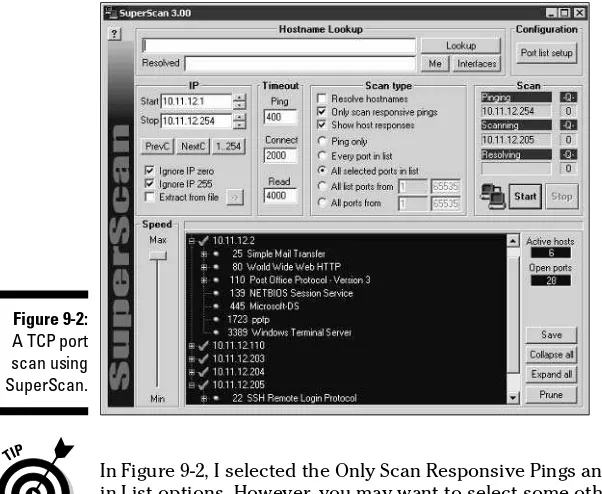
Wiley Publishing Hacking for Dummies [2004]
Teks penuh
Gambar
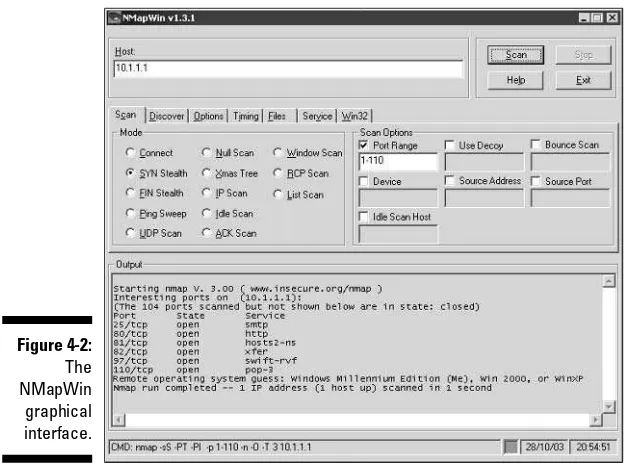
Garis besar
Dokumen terkait
It’s well and good to encrypt your data, but you also have to make sure that you really know who you are working with on the other end of the Internet... Chapter 8: Securing
Click the plus sign to expand the item into a list of playlists, and select a playlist to see the audio tracks or video clips it contains.. ✦ Radio Tuner Presets: Lists streaming
⻬ Make internal resources available: Although the primary purpose of a firewall is to prevent unwanted network traffic from passing through it, you can also configure many firewalls
Drag Customer.Region from the Report Fields pane down to the blank pane at the lower right of Group Selection Formula Editor. You want to set that field equal to
(It isn’t as tough as it sounds.) Then you attempt to compile the program again — you recompile and relink. ⻬ The compiler translates the information in the source code file
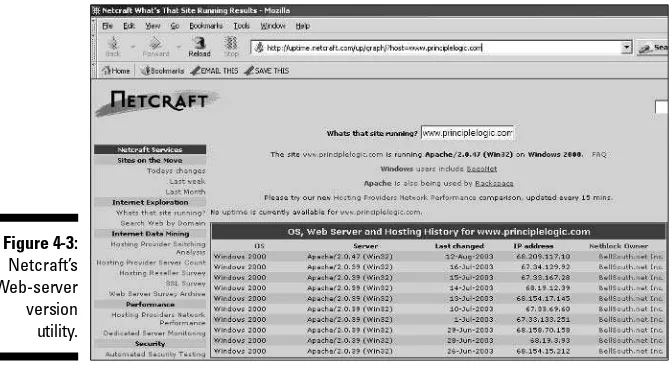
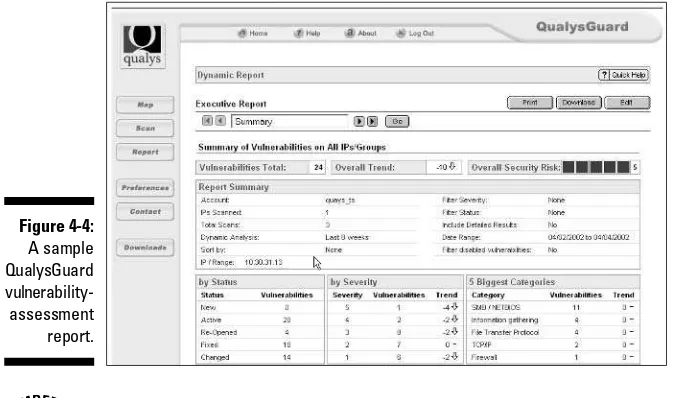
It’s superior to guessing; by gathering information on the software (refer to Chap- ter 15), you’re more than prepared to know exactly what type of hardware you need to successfully
In older versions of Windows, the System Monitor program was used to check up on resources and see how much of them were left and what Windows was using.. In Windows XP, the
We show you two operating system methods to recover these files, as well as Recovery Manager backup and restore operations, in this chapter’s “Recovering Your Oracle