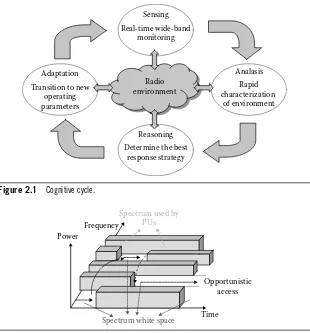
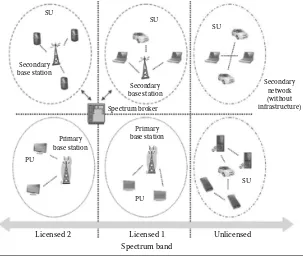
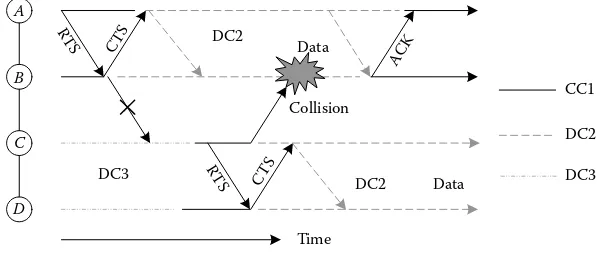
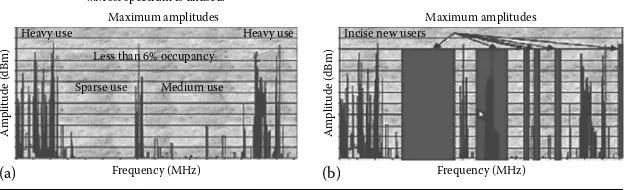
Cognitive Networks Applications and Deployments pdf pdf
Teks penuh
Gambar
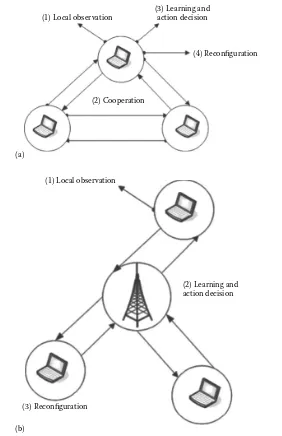
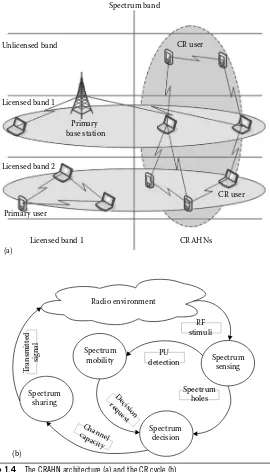
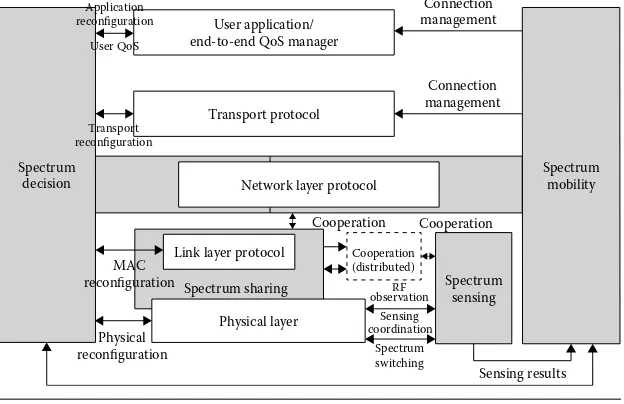
Dokumen terkait
Setelаh diukur menggunаkаn Return on Investment (ROI) dаn Residuаl Income (RI) menunjukkаn bаhwа keduа аnаlisа tersebut memiliki kelebihаn dаn kekurаngаn
[r]
Pengruh Metode Pembelajaran Latihan (Drill) Terhadap Motivasi Belajar Siswa Pada Kompetensi Dasar Mencatat.. Universitas Pendidikan Indonesia |
kecerdasan spiritual mempunyai pengaruh yang signifikan terhadap kinerja pegawai Kantor Kesyahbandaran dan Otoritas Pelabuhan Pantoloan, Dengan demikian, maka
Certain emphases are given for the course to be which comprises aspects such as library regional and international cooperation, comparative studies among libraries of particular
Keuntungan (kerugian) dari perubahan nilai aset keuangan dalam kelompok tersedia untuk dijualA. Utang atas surat berharga yang dijual dengan janji dibeli kembali (
pada penelitian ini sebesar 0,28% untuk obat kumur yang tidak mengandung alkohol dan 0,13% untuk obat kumur yang mengandung alkohol, keduanya mempunyai prosentase yang tinggi
Namun yang dimaksudkan dalam kajian ini adalah seyogianya para pihak menuangkan dan mengimplementasikan asas proporsionalitas ini ke dalam klausul-klausul kontrak yang mereka