Security Concepts for Embedded Systems wasicek embedded security
Teks penuh
Gambar
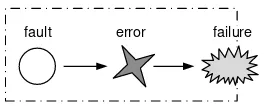
![Figure 4: Vulnerability life cycle after Schneier [72].](https://thumb-ap.123doks.com/thumbv2/123dok/3943959.1887379/12.595.209.432.128.194/figure-vulnerability-life-cycle-after-schneier.webp)
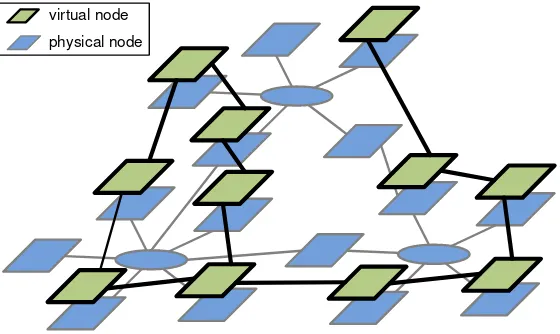
![Figure 5: Attacks on Embedded Systems after [69]](https://thumb-ap.123doks.com/thumbv2/123dok/3943959.1887379/15.595.134.417.343.528/figure-attacks-on-embedded-systems-after.webp)
Dokumen terkait
1) Memberikan informasi kepada pihak sekolah terkait akar permasalahan rendahnya daya saing di SMA Kristen 2 Salatiga. 2) Memberikan masukan kepada pihak sekolah berupa
Kesimpulan yang diperoleh dari penelitian ini adalah bahwa dengan menggunakan pembelajaranIndex Card Match dapat meningkatkan sikap kerja keras dan prestasi belajar
Untuk itu dimohon kehadiran saudara untuk pembuktian kualifikasi dimaksud dengan membawa seluruh dokumen kualifikasi asli / telah dilegalisir oleh pihak yang berwenang serta
Demikian pula sebaliknya, pecahan desimal dapat dinyatakan dalam bentuk pecahan biasa atau pecahan campuran. Persen mempunyai arti
Uraian dari kedua penulis tersebut menjelaskan bahwa konsep agraria sejak beribu-ribu tahun dipahami dalam arti yang lebih luas dari sekedar tanah atau tanah pertanian..
Pada hari ini Kamis tanggal Tujuh bulan Mei tahun Dua Ribu Lima Belas Unit Layanan Pengadaan Kabupaten Gunung Mas Tahun Anggaran 2015 Kelompok Kerja (Pokja) IV telah
[r]
Hasil rapat Pokja jasa ULP Polda NTB, paket pekerjaan Pengadaan (Catering) makan dan extra fooding siswa Diktukba Polri T.A 2014 SPN Polda NTB adalah menyepakati
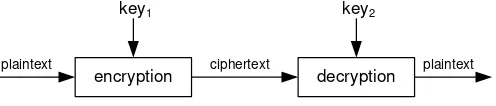
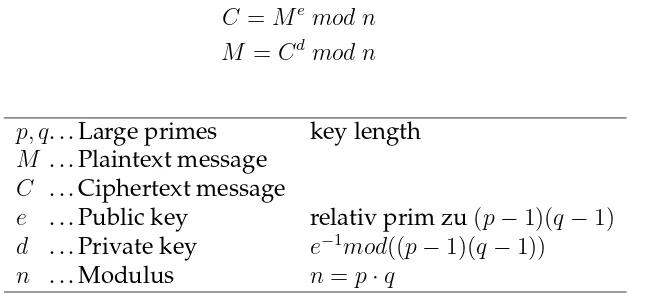
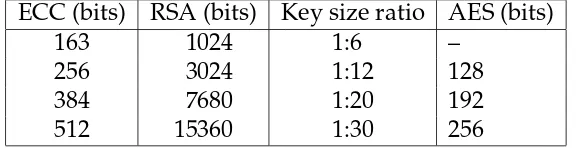
![Table 7: Average ECC and RSA execution times on the ATmega128 andthe CC1010 after [32]](https://thumb-ap.123doks.com/thumbv2/123dok/3943959.1887379/35.595.87.467.128.239/table-average-ecc-rsa-execution-times-atmega-andthe.webp)