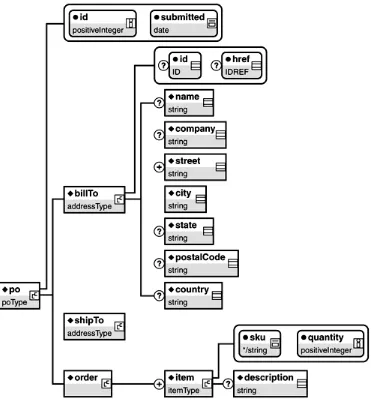
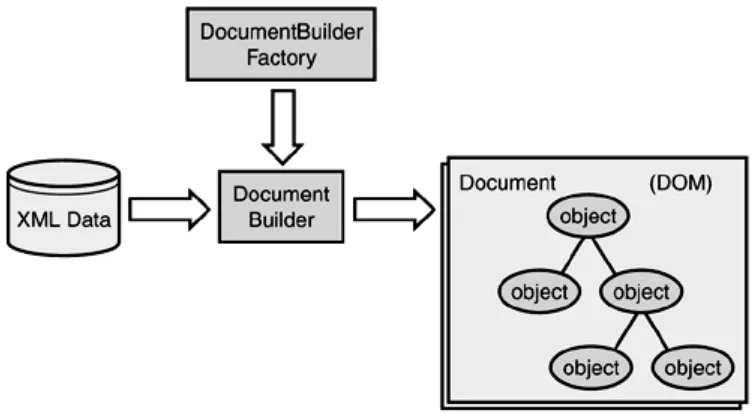
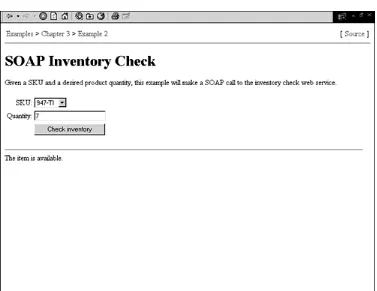
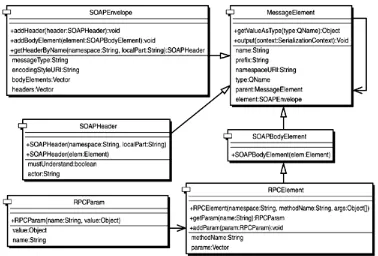
Building web serivices with Java making sencse of XML
Teks penuh
Gambar
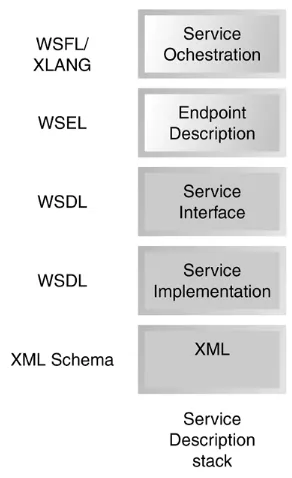
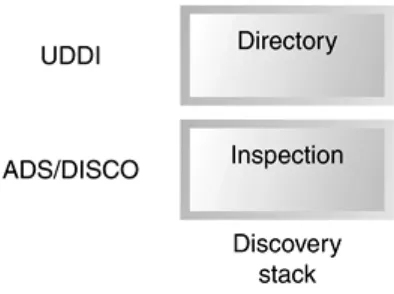
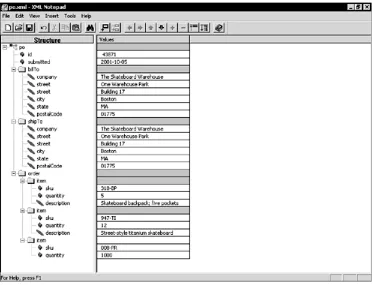
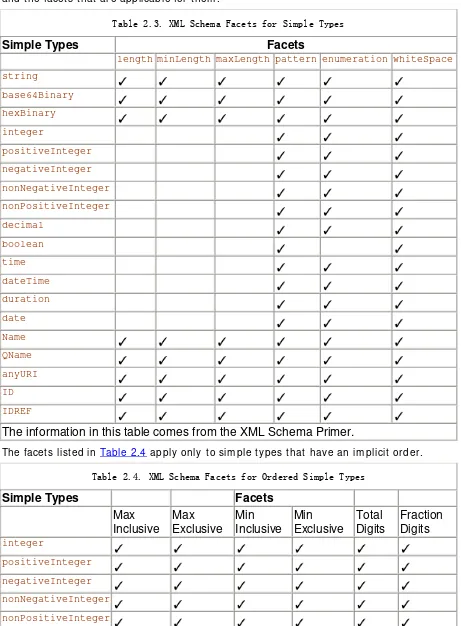
Dokumen terkait
Kelompok Kerja Jasa Konsultansi Unit Layanan Pengadaan Barang/Jasa Kabupaten Lamandau mengumumkan pemenang seleksi sederhana untuk Pekerjaan Jasa.. Pengawasan Pembangunan Gedung
Each homework problem will be scored using the following 4-point rubric and your final homework score will be the average of each item level score: 4 points (Excellent)..
formulir isian kualifikasi yang di input di dalam Sistem Pengadaan Secara Elektronik (SPSE) pada alamat website LPSE, sesuai yang tertuang dalam Dokumen
[r]
Keterlibatan dari Departemen Kesehatan diharapkan dapat memberikan kesadaran dan pemahaman kepada masyarakat akan pentingnya menjaga kesehatan dan ketahanan tubuh khususnya dalam
Jumlah konversi pada biaya sudah sesuai dengan metode pembayaran PAMSIMAS Desa Rejosari dengan nilai rata- rata kesalahan sistem 0.003 % dan sistem monitoring SMS gateway
KADAR HS-CRP PADA PASIEN DISPEPSIA DENGAN INFEKSI HELICOBACTER PYLORI DIBANDINGKAN DENGAN TANPA INFEKSI2.
Formulir Penjualan Kembali Unit Penyertaan yang telah lengkap dan diterima secara baik ( in complete application ) serta telah memenuhi persyaratan dan ketentuan yang tercantum