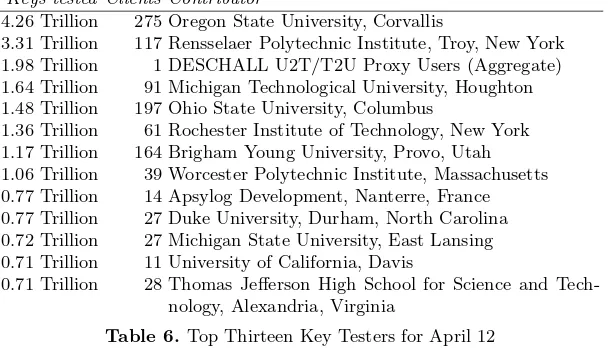
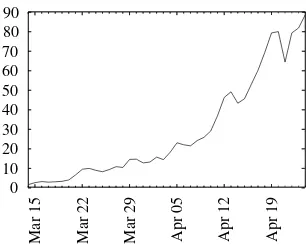
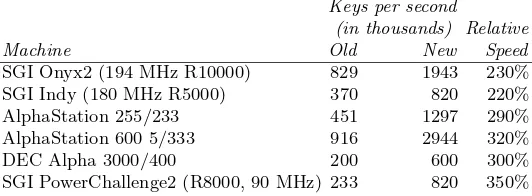
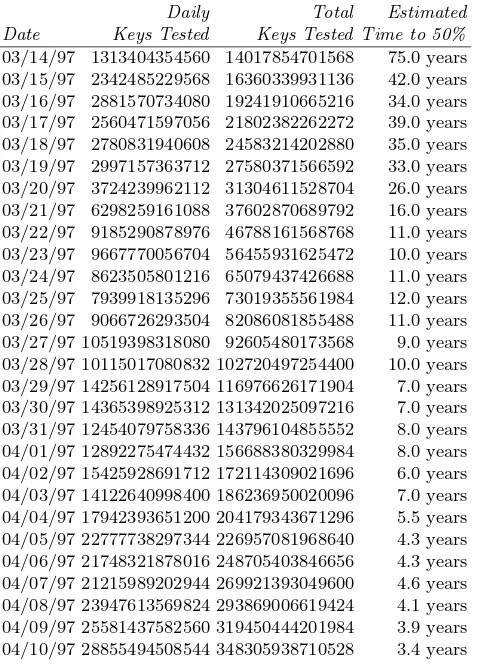
Brute Force Cracking the DES pdf pdf
Teks penuh
Gambar

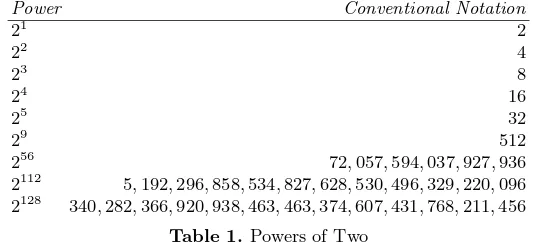

Garis besar
Dokumen terkait
1 (a) and (b) show the two-dimensional (2D) profiles and the islands size distribution graphs of the surface morphology of Fe(III)–porphyrin thin layers (sample B) on ITO-coated
Hasil yang sama didapatkan pada penelitan Muhialdin dan Hassan (2011) yang mengungkapkan bahwa /EUHYLV G004, /IHUPHQWXP Te007 dan 3HGLRFRFFXV SHQWRVDFHXV Te010 menunjukkan
Kuala Jambi Kabupaten Tanjung Jabung Timur Tahun Anggaran 2014, untuk Paket Pekerjaan tersebut diatas telah dilaksanakan Pembukaan Penawaran pada Tanggal 03 Agustus 2014,
Berdasarkan hasil Uji Wilcoxon keseluruhan citra dengan membandingkan nilai p- value secara keseluruhan antara sekuen 2D thick slab single shot fast spin echo
[r]
memimpin, mengatur, membina dan mengendalikan pelaksanaan program dan kegiatan serta penetapan kebijakan teknis pada Dinas yang meliputi Sekretariat, Bidang
Bila material rusak dalam proses pengerjaan tidak dapat diganti atau mengulang dengan material baru.. Setelah uji visual akan dilanjutkan dengan uji hydro ( Hydro
Dengan demikian, pendidikan kejuruan merupakan penyelenggaraan jalur pendidikan formal yang dilaksanakan pada jenjang pendidikan tingkat menengah, yaitu: