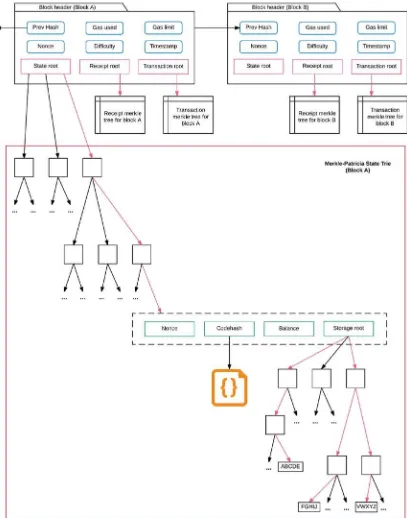
Blockchain Enabled Applications by Vikram Dhillon
Teks penuh
Gambar
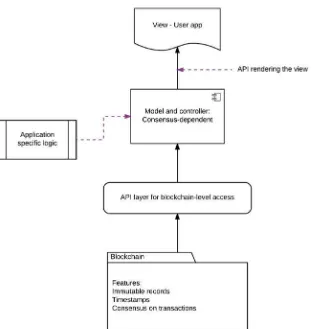
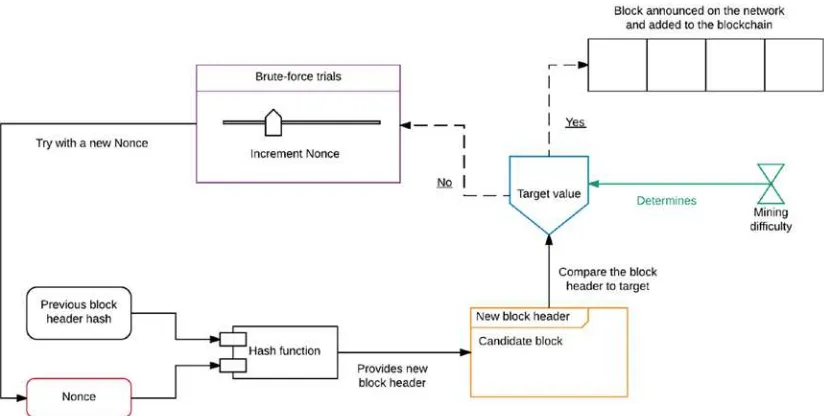
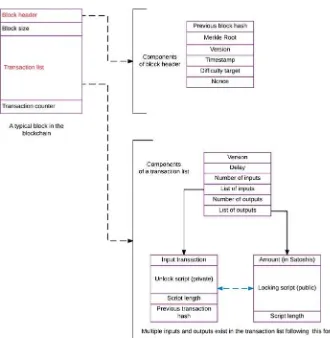
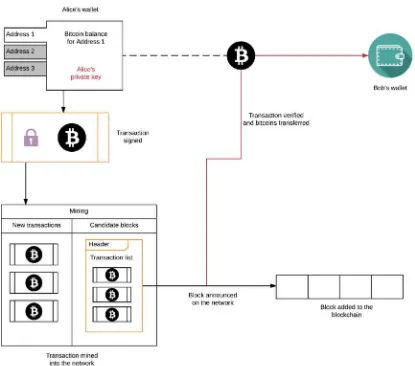
Dokumen terkait
Namun secara spesiik yang dimaksud pekerja sosial profesional pada Bagian ketiga Undang-Undang Nomor 11 Tahun 2012 tentang Sistem Peradilan Pidana Anak Pasal 66
Jika pada tanggal / waktu tersebut diatas Saudara atau yang mewakili Saudara (yang ditunjukkan dengan Surat Kuasa dari Perusahaan ) tidak dapat hadir dan/atau
3) Pembuktian kualifikasi untuk menilai pengalaman yang sejenis dan besaran nilai pekerjaan yang sesuai dengan nilai pekerjaan yang akan dikompetisikan dilakukan
Pertama, padi adalah pangan yang disukai oleh hampir seluruh lapisan masyarakat Merauke, bukan hanya pendatang, tetapi juga masyarakat asli, termasuk penduduk Papua Nugini yang
Catatan : Agar membawa dokumen perusahaan asli sesuai dalam isian kualifikasi serta menyerahkan rekaman/copy-nyaM. Demikian undangan dari kami dan atas perhatiannya
[r]
Restoration efforts could, in some cases, help spread invasive species, but until very recently the USACE had not consid- ered invasive species in project planning
MANFAAT HASIL BELAJAR FASHION MERCHANDISING SEBAGAI KESIAPAN MENJADI FASHION MERCHANDISER DI SPECIAL STORE. DISETUJUI DAN DISAHKAN