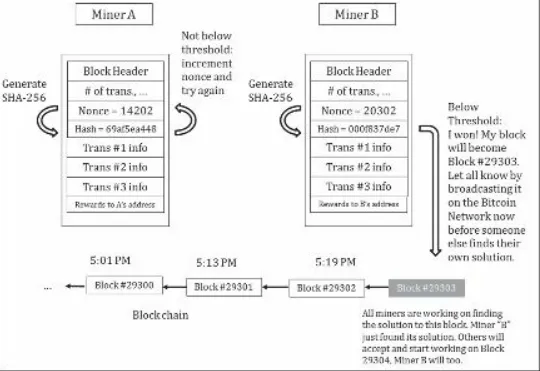
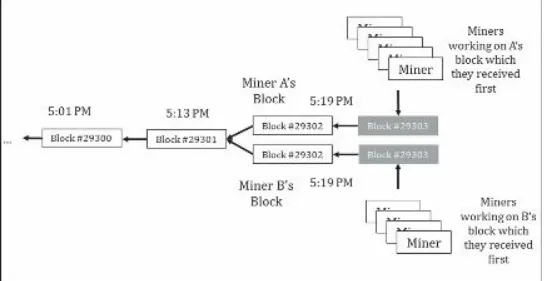
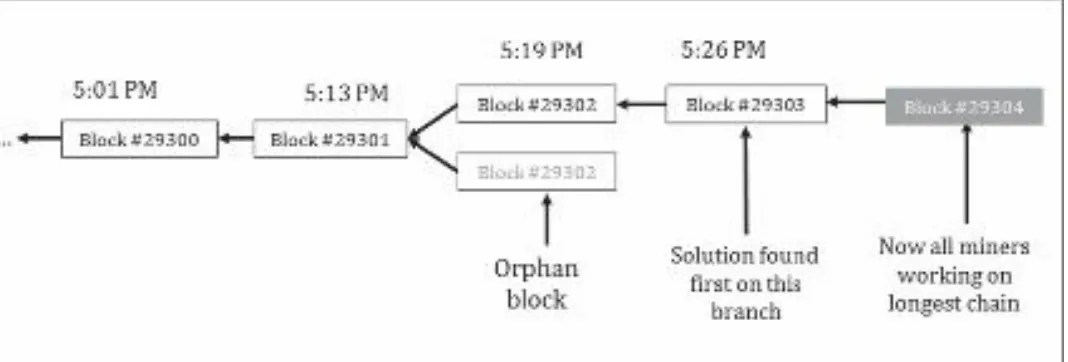
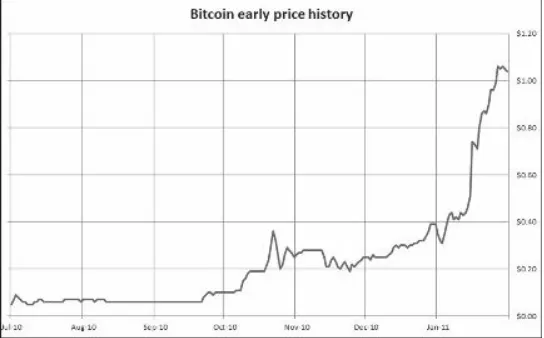
BitCoin and Cryptocurrencies The Book Of Satoshi The Collected Writings of Bitcoin Creator Satoshi Nakamoto Jun 2014 pdf
Teks penuh
Gambar
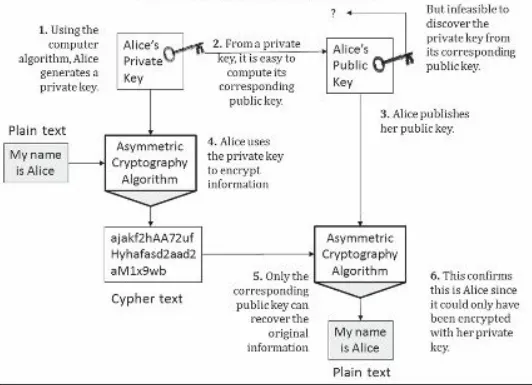
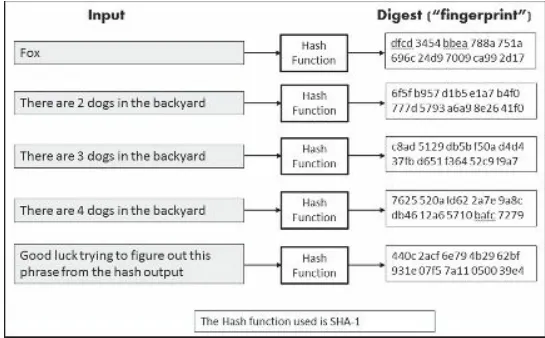
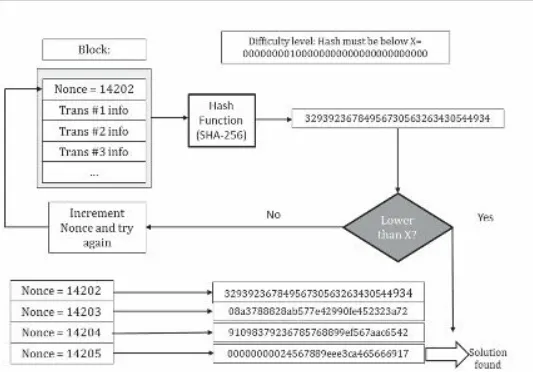
Dokumen terkait
Dilihat dari kondisi topografinya Daerah Aliran Sungai (DAS) Kali Ngotok bagian hulu berada di Kabupaten Jombang dan sebagian kecil dihilir berada di
Adapun hal yang menjadi alasan untuk melakukan penelitian efektivitas pendekatan cognitive behavioral therapy dengan setting kelompok untuk meningkatkan motivasi
Pada awalnya Instagram sendiri berkembang dari aplikasi iPhone untuk berbagi foto hingga sekarang menjadi sebuah perusahaan sosial internet yang berkembang.. iPhone
home pain. So that later hospital side and or individual owning this data will feel getting a disadvantage. To anticipate from undesirable things like forgery of data,
THE INFLUENCE OF PROJECT BASED LEARNING TOWARD ELECTRICAL MACHINE AND ENERGY CONVERSION STUDENT ACHIEVEMENT OF VOCATIONAL HIGH SCHOOL 1 PADANG Nurzamaliah Afifah,Ambiyar
Along with the conclusions, propose the following suggestions: (1) the school management should monitor the performance of teachers through classroom
Telah dikembangkan model bahan ajar, yang karakteristiknya, didasari pada karak- teristik pelajaran fisika sesuai dengan tuntutan kurikulum 2013 dari sisi konten,
Data yang digunakan dalam penelitian ini adalah data sekunder dari perusahaan di Indonesia yang melakukan proses akuisisi selama periode 2009- 2012 meliputi