Introduction to Networks v6 Companion Guide pdf pdf
Teks penuh
Gambar
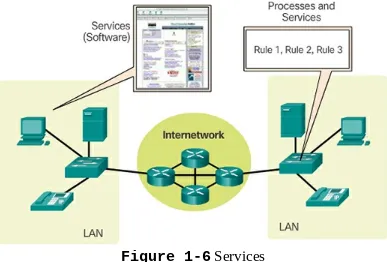
Dokumen terkait
● Training is the act of presenting the network with some sample data and modifying the weights to better approximate the desired functionn. ● There are two main types
For example, before a host interface has been allocated an IP address, it sends a Dynamic Host Con fi guration Protocol (DHCP) request packet with the Limited Broadcast Address as
Components within the layered architecture pattern are organized into horizontal layers, each layer performing a specific role within the application (e.g., presentation logic
“Generally speaking, it’s fair to say existing networks are ready for IoT traffic, because IoT traffic isn’t all that different from normal IP (Internet Protocol) traffic,”
The network layer does not care about what kind of link protocols are used on route between the source and the destination.. Figure 1.7: Network
( I n an 802.11 net work, t he base st at ions are called access point s .) The infrast ruct ure side of a wireless net work, however, is qualit at ively t he sam e whet her you
We analysed the performances of the proposed protocol with different scenarios in comparison with DEEC, DDEEC and EDEEC protocols in terms of criteria, alive nodes during the network
Match the following to one or more layers of the TCP/IP protocol suite: a route determination b connection to transmission media c providing services for the end user d creating user