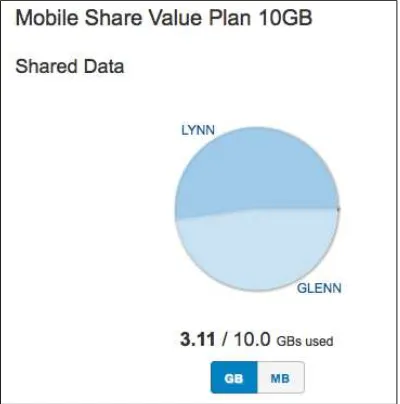
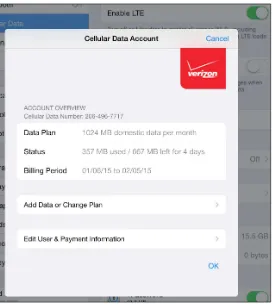
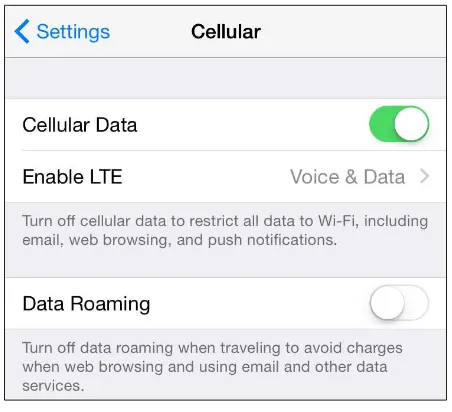
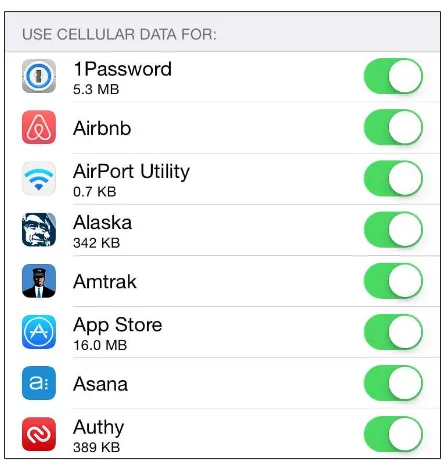
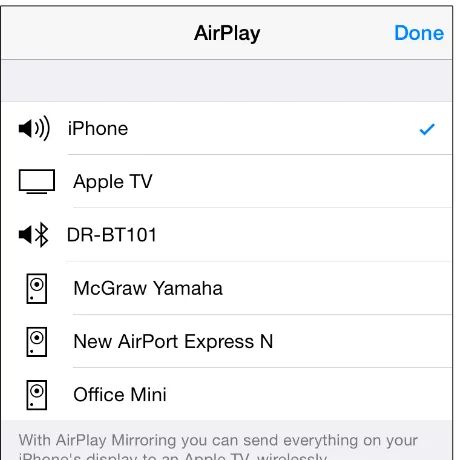
A Practical Guide to Networking and Security in iOS 8 pdf pdf
Teks penuh
Gambar


Dokumen terkait
[r]
Pada hari Rabu Tanggal Dua Puluh Tiga Bulan Juni Tahun Dua Ribu Sebelas, kami yang bertanda tangan di bawah ini Pokja Pengadaan Barang, Pekerjaaan Konstruksi dan Jasa
Dengan ini disampaikan bahwa berdasarkan Surat Penetapan Pemenang Nomor : 142/08/POKJA-BLPBJ.MKS/VII/2017 Tanggal 05 Juli 2017, Kami Pokja BLP Bagian Layanan
Standar Dokumen Pengadaan Secara Elektronik. Pengadaan
[r]
Hal-hal yang harus diperhatikan dalam penapisan kedelai toleran salinitas adalah: (1) Pengawasan/kontrol kondisi media dan lingkungan dilakukan dengan pengukuran DHL tanah/ media
Pertidaksamaan kuadrat diselesaikan dengan bantuan garis bilangan, yaitu dengan menguji pada masing-masing daerah pada garis bilangan dengan mencantumkan akar-akar persamaan
memiliki perilaku afiliasi yang rendah, jarang melakukan interaksiB. dengan orang lain, lebih suka berdiam diri, dan tidak peduli